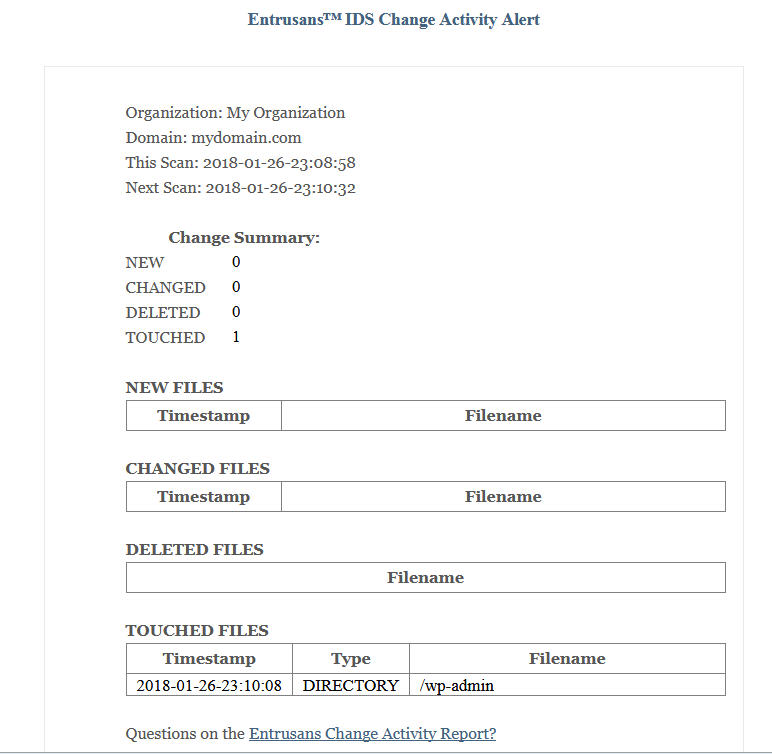
The EntrusansTM IDS Change Activity Report is your primary tool for detecting suspicious files on your website. The report is organized into five sections:
- The Change Summary section shows a quick picture of the scope of changes for the period.
- The New Files section lists all new files found in a scan. Files placed by hackers will be listed here.
- The Changed Files section lists all files that have changed in a scan. Malicious code is often placed in core application files by hackers.
- The Deleted Files section lists all files that have been deleted in a scan. Hackers are known to delete files on websites especially security plugins.
- The Touched Files section lists files and directories where the timestamps have changed. Hackers can gain entry to a website and then delete their actions to avoid detection.
The Change Activity Report has 5 sections for quick assessment of change activity on a website. Depending on the application software installed on the website a Change Activity emails may arrive every scan cycle. Examples of continuously changing files could include continuously updated log files, cache files and any files created or deleted by application programs. The Entrusans IDS provides filters to exclude files or directories from reported as changed where the website owner is confident these files present low risk of compromise.
If your website changes are infrequent due to periodic software upgrades or routine updates of image files you will receive emails only when these changes take place. Review all of the changes to confirm they were authorized as one of those changes can be due to a compromise. In the event that it is a compromise you will have a record of the changes the hacker made to your website.
Change Summary
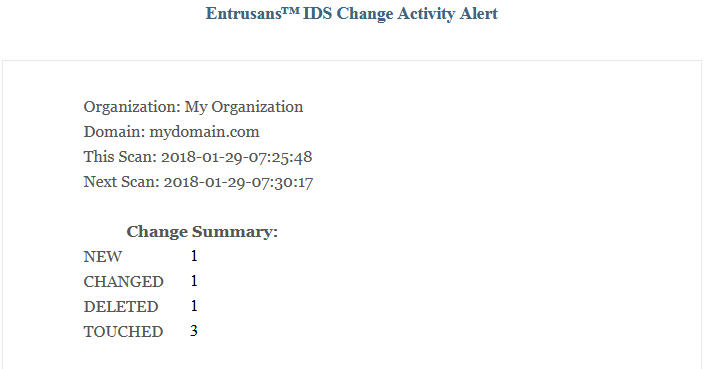
The Change Summary section provides a quick overview of the scope of a change in the website. This summary will vary based on the activity on the site. For example a major software upgrade for applications will result in larger numbers in multiple report sections including New, Changed, Touched and possibly Deleted. Small numbers are common for applications that use log or cache files or routine site maintenance. Over time a change pattern for the website will emerge enabling the detection of unusual activity.
New Files
The New Files section is the first stop for spotting suspicious change activity. The filenames listed in the diagram below were made up to illustrate how obvious an unauthorized file can appear. In this example a hacker has managed to upload a file to the site indicating the website has been compromised. Hackers are rarely that friendly and MadTek has often detected hacker files in multiple locations on websites. One common hacker technique is to place executable files in image directories using existing image names only with an executable extension, for example we would find my-latest-product.jpg and my-latest-product.php. The Entrusans IDS was designed to quickly identify suspicious files.

Changed Files
It is common for hackers to add malicious code to existing files on the website following a compromise. Identifying these files is critical to efficient and effective recovery of a compromised website. Missing only one infected file can lead to a subsequent compromise. Many tools are available for scanning files for infection, but only for known signatures. Hackers are clever and continuously introduce new, unknown, signatures. Knowing that a file has changed is a unique and powerful tool in identifying compromised files.

Deleted Files
MadTek has direct experience with hackers disabling security plugins. One technique is to simply delete the security plugin files. Use the deleted files section to review any deleted files. Normal activity on the website will result in files being deleted and those files be listed in the section. Applications such as Drupal, WordPress and Joomla have specific locations where security plugins are located. Hacker actions to delete files for security plugins will be reported in the Deleted Files section. When examining the Deleted Files section also look for any files that have changed in any security plugin.
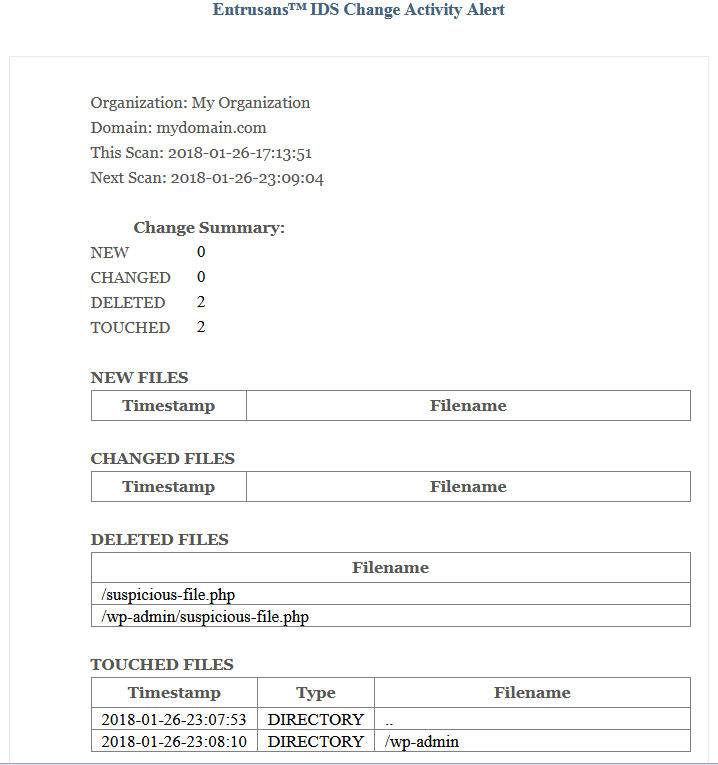
Touched Files
The Touched Files section was designed to detect the use case where a hacker exploits a website vulnerability within the Entrusans IDS scan cycle, uploads a malicious file, uses the website for nefarious purposes and then the malicious file deletes itself to avoid detection. The hacker chooses not to modify any files on the site in order to leave minimal traces. This activity could be automated so that the hacker could continuously use the website until the vulnerability is uncovered by the website owner and fixed.
In this case there is residual information that can indicate the use of a vulnerability to upload and delete a file repeatedly. Although a hacker may upload a file that deletes itself the timestamp of the directory where the file is uploaded will change. Without administrator privileges the hacker cannot reset the timestamp of the directory. If a directory timestamp is reported as changed on every scan cycle it is a potential indicator of malicious activity and should be investigated. Such activity could be legitimate and due to an application creating and deleting files in normal operation. The webstie owner can use the Touched Files section to expose such application behavior and deal accordingly so that this type of difficult to detect compromise can be detected.